In today’s digital age, where secrets fly through texts and whispers travel on Wi-Fi, safeguarding our conversations is paramount. Apple’s iMessage offers robust encryption, but for the truly privacy-conscious, there’s an extra layer of security: contact key verification. This feature acts like a secret handshake, confirming you’re truly chatting with the person you think you are. This guide unpacks Contact Key Verification on your iPhone, transforming it from a technical term to a shield for your messages.
Why use contact key verification?
Imagine your iMessages as top-secret documents locked away in a vault. Standard iMessage encryption acts as the first line of defense, scrambling messages to render them unreadable by anyone except you and the recipient. However, even the most secure vaults can have vulnerabilities. Malicious actors could exploit weaknesses or impersonate trusted contacts to gain access.

Here’s where contact key verification steps in, providing an extra layer of security. Each device participating in an iMessage conversation possesses a unique cryptographic key—a complex digital code acting as a virtual fingerprint. When enabled, your iPhone and your contact’s iPhone securely exchange these keys. The verification process then compares them against trusted keys stored on Apple’s servers. If the keys match, a green checkmark appears, signifying you’re communicating with the intended person. This throws a wrench into the plans of attackers, as impersonation would require not only replicating their Apple ID and phone number but also forging their unique key—a near-impossible feat.
Think of it like this: without contact key verification, anyone with your phone number or Apple ID could impersonate you. By enabling verification, you add an extra layer of authentication, ensuring only someone with the correct “digital key” can access your iMessage vault.
Enable contact key verification
Turning on contact key verification is a breeze.
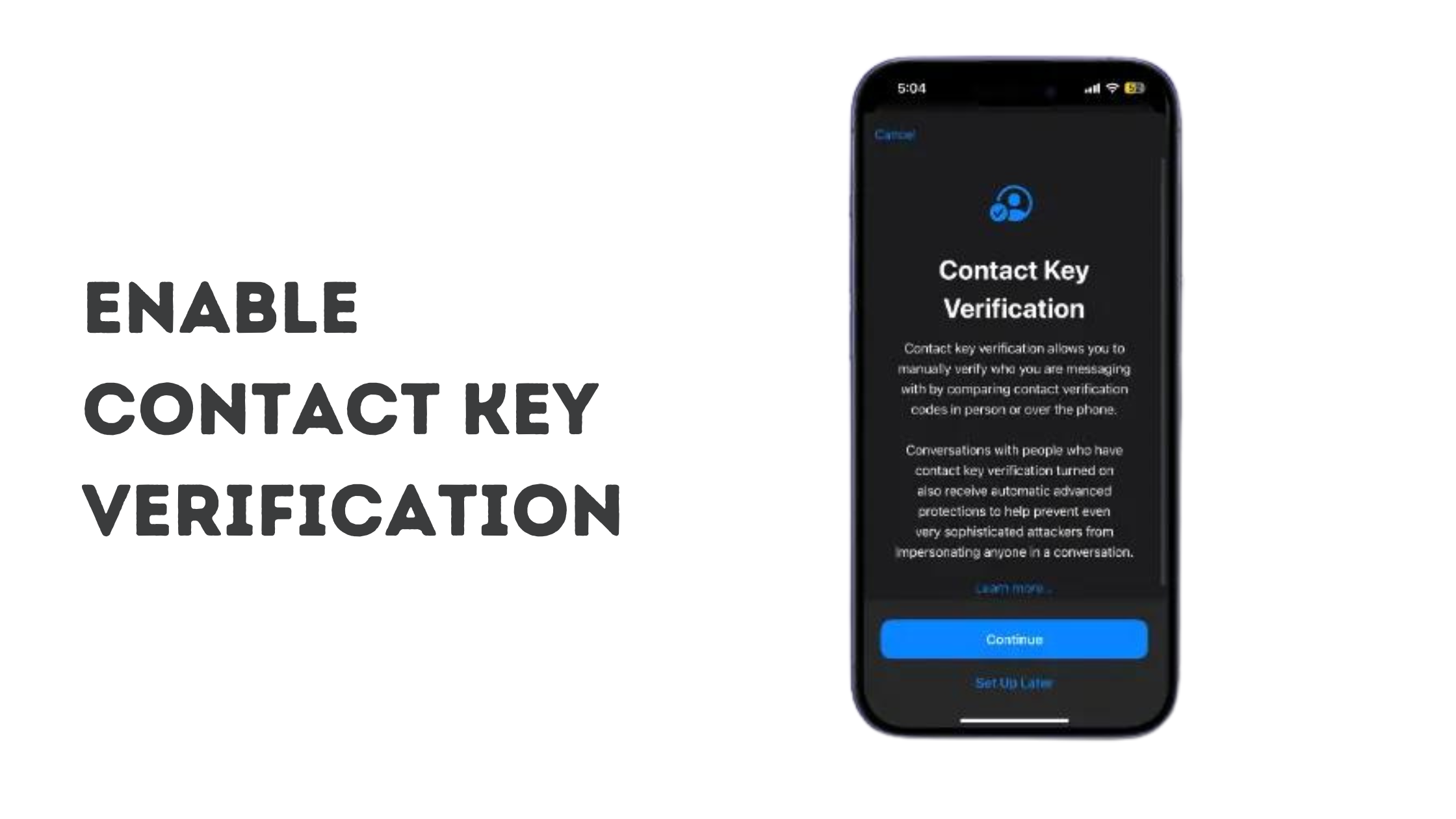
- Unlock Your Digital Vault: Locate the Settings app, the control center for your iPhone, and tap on it (it resembles a gray gear icon).
- Navigating to Your Apple ID: Scroll down and tap on your Apple ID, typically your email address displayed at the top of Settings.
- Finding the Secret Handshake: Tap on your Apple ID to open a submenu with various settings. Locate the option labeled “Contact Key Verification”—this is the hidden gem!
- Enable Verification: Toggle the switch next to “Contact Key Verification” to the “On” position. Your iPhone will display a confirmation message. Tap “Continue” to proceed.
Congratulations! You’ve successfully activated contact key verification for your iMessages. Now, your iPhone will automatically verify your contacts’ keys, adding an extra layer of security to your chats.
Also, check out: 10 Ways to Fix It When Your iPhone Charging Port Isn’t Working
Verifying your own identity for others
While contact key verification safeguards your outgoing messages, you might also want to verify your identity for others, especially when initiating contact with someone new. Here’s how your contacts can verify your identity:
- Opening the Conversation Thread: Within the Messages app, locate the conversation thread with the person you want to verify your identity for.
- Accessing your contact information: Tap on your name or profile picture at the top of the conversation window. This will display your contact information card.
- Sharing Your Encryption Details: On the contact information card, scroll down and tap on “Encryption.” Within this section, they can tap on “View Verification” to display your cryptographic key.
There are two ways your contacts can verify your identity using this code: - In-Person Verification: If you’re meeting the contact in person, you can compare the displayed code on your iPhone with the code displayed on theirs. If the codes match, they can be confident they’re communicating with you.
- Verification Through Secure Communication: Alternatively, if an in-person meeting isn’t feasible, consider verifying the code through a secure communication channel, such as a FaceTime call or a phone call made through a trusted landline. Once connected, verbally share the displayed code and confirm if it matches on both devices.
By sharing your cryptographic key and using one of these verification methods, you can ensure your contacts are communicating with the real you.
Verifying the Identity of Others
While enabling contact key verification protects your outgoing messages, you might also want to verify the identities of incoming messages, especially when dealing with new contacts. Here’s how to verify the identity of someone you’re chatting with on iMessage:
- Opening the Conversation Thread: Locate the conversation thread with the contact you wish to verify within the Messages app.
- Accessing contact information: Tap on the contact’s name or profile picture at the top of the conversation window. This will display their contact information card.
- Demystifying the Code: On the contact information card, scroll down and tap on “Encryption.” Within this section, tap on “View Verification” to display their cryptographic key.
There are two ways to verify your contact’s identity using this code: - In-Person Verification: If you’re meeting the contact in person, compare the displayed code on your iPhone with the code displayed on their iPhone. If the codes match, you can be confident that you’re communicating with the right person. Think of it like a high-security handshake: both parties need to possess the correct digital code to establish a secure connection.
- Verification Through Secure Communication: Alternatively, if an in-person meeting isn’t feasible, consider verifying the code through a secure communication channel, such as a FaceTime call or a phone call made through a trusted landline. Once connected, verbally share the displayed code and confirm if it matches on both devices. Imagine this as a two-factor authentication process, adding an extra layer of security by utilizing both your iPhone and another trusted communication method.
By verifying the cryptographic keys using either of these methods, you can ensure that you’re indeed communicating with the intended recipient and not a potential impersonator. This extra layer of verification can be invaluable when dealing with sensitive information or communicating with new contacts.
Additional Steps for Public Verification Codes
Occasionally, you might encounter situations where businesses or organizations provide public verification codes as part of their authentication process. These codes can be less secure than individual verification methods like contact key verification. Here’s what to do when you encounter a public verification code:
- Match the Code with a Hawk Eye: Make sure the code displayed on your screen matches exactly what the business or organization provided. A single character difference could indicate a phishing attempt designed to steal your information. Double-check and triple-check the code before entering it. Think of it like a puzzle piece; if it doesn’t fit perfectly, something fishy might be going on.
- Be Wary, Trust, But Verify: Public verification codes are generally less secure than individual verification methods. They might be vulnerable to interception by malicious actors. If possible, opt for other verification methods offered by the business, like email verification or a phone call to a known number. This reduces the risk of exposing your information through a potentially compromised public code. Remember, it’s always better to be safe than sorry when it comes to your online security.
- Knowledge is power. Research Before You Leap: Before entering any public verification code, take a moment to research the business or organization requesting it. Are they a legitimate entity with a good reputation? Is there any information online suggesting they might be engaged in phishing scams? A little research can go a long way toward protecting your privacy and security. Think of it like investigating a company before doing business with them; it’s important to know who you’re dealing with online.
By exercising caution and following these guidelines, you can navigate situations involving public verification codes with greater peace of mind. Remember, when in doubt, it’s always best to err on the side of caution and avoid entering any codes you’re unsure about.
If You Receive a Contact Key Verification Alert
Ever see a pop-up about contact key verification while using iMessage? Don’t panic! These alerts can be helpful indicators of potential security concerns, and understanding them is crucial for maintaining secure communication.
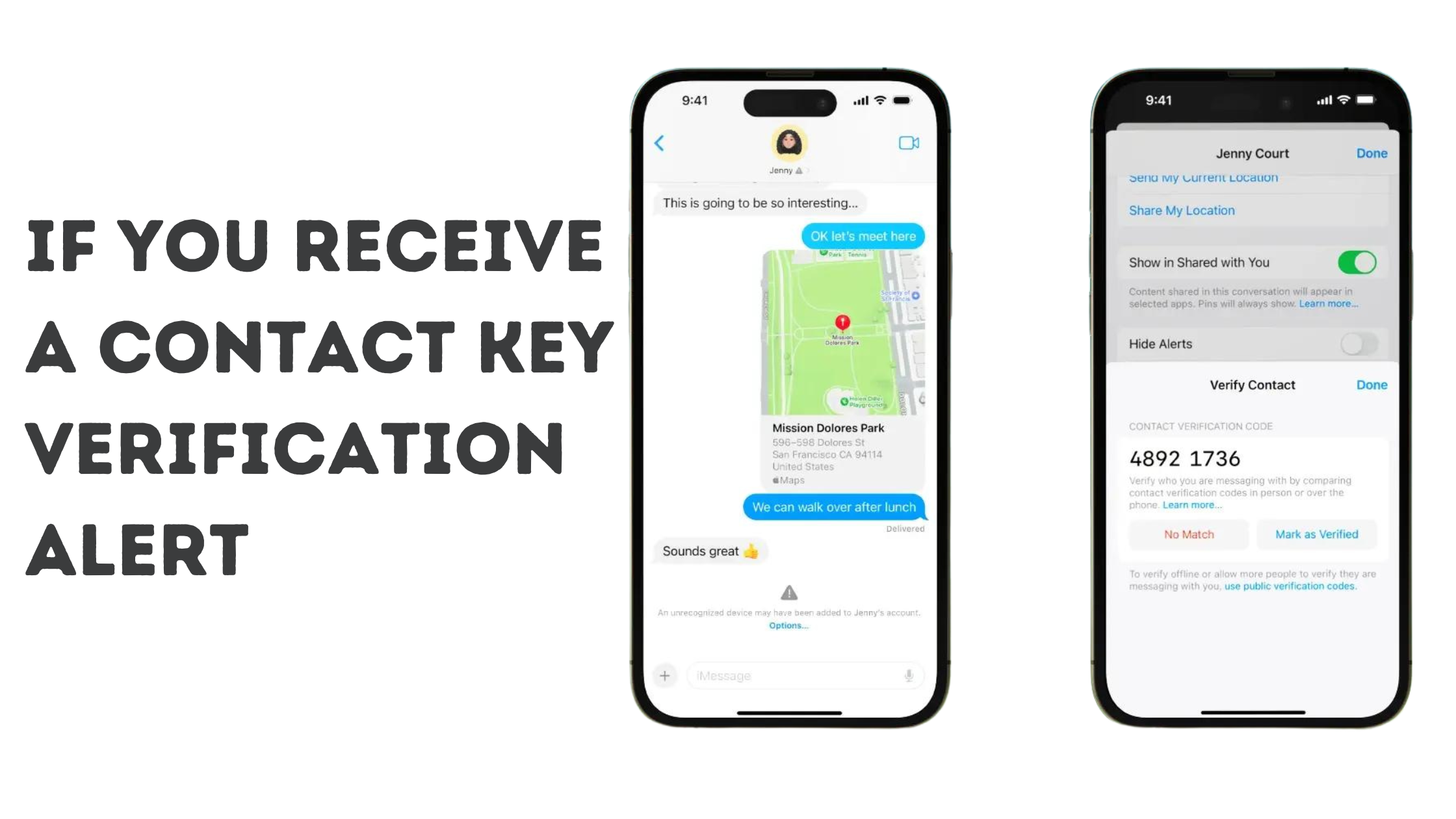
Here’s how to interpret these alerts:
- Scrutinize the Alert Like a Detective: The first and most important step is to verify the legitimacy of the alert itself. Scammers might try to create fake notifications to trick you into revealing information. Look for any signs that the alert might be suspicious, such as typos or grammatical errors. If you’re unsure about the authenticity of the alert, it’s best to contact Apple Support for clarification. Think of it like a suspicious email—don’t click on any links or enter any information until you’ve confirmed it’s legitimate.
- Follow the Steps with Care: If the alert appears to be legitimate, follow the steps displayed on the screen carefully. These steps might involve verifying the identity of your contact using one of the methods described earlier, or they might provide instructions on how to secure your conversation if a potential security risk has been detected. By following the correct steps, you can address the issue and ensure that your messages remain secure. Imagine it like a fire alarm; if it goes off, you need to take action to identify and address the potential threat.
- Staying vigilant is key: Receiving a contact key verification alert, especially if unexpected, can be a good reminder to be extra cautious about your online security. Here are some additional steps you can take to further enhance the security of your iMessage communication:
- Review your privacy settings regularly: Schedule regular check-ins with your iPhone’s privacy settings. Review who has access to your data, what information is shared with apps, and ensure everything is configured according to your comfort level. Think of it like reviewing the security measures of your home; it’s important to check them periodically to identify any vulnerabilities.
- Be cautious about sharing personal information online: Limit the amount of personal information you share online, especially on public platforms or with unknown contacts. Consider using separate email addresses for personal and professional communication. Remember, the less information you share online, the less susceptible you are to targeted attacks.
- Educate Yourself About Phishing Scams: In the digital jungle, phishing scams lurk like cunning predators, waiting to pounce on unsuspecting prey and snatch away valuable personal information. Learn to recognize the signs of phishing attempts, such as suspicious emails, unsolicited links, and urgent requests for information. Think of it like learning self-defense techniques: the more you know about online threats, the better equipped you are to handle them.
- Update Your iPhone Regularly: Software updates often include security patches that address vulnerabilities in the system. Keeping your iPhone updated with the latest software ensures it has the most up-to-date defenses against potential attacks. Imagine it like patching holes in your walls—updates help seal potential security weak points.
By following these steps and using contact key verification, you can significantly enhance the security of your iMessages. Remember, online security is an ongoing process, not a one-time fix. By staying vigilant and taking proactive measures, you can transform your iPhone into a secure fortress for your messages, ensuring your conversations remain private and protected.
